threat test support package|intel support to targeting : warehouse A threat is defined as an adversary’s intent, capability and opportunity to target, exploit or compromise U.S. Government critical technologies, programs or information. . Note: Interaction to Next Paint (INP) is a pending Core .
{plog:ftitle_list}
WEBPixel art gallery created with the Pixilart Drawing Application - Pixilart, Free Online Pixel Drawing Application!
A threat is defined as an adversary’s intent, capability and opportunity to target, exploit or compromise U.S. Government critical technologies, programs or information. .Identify and submit command threat support requirements and request intelligence reports through the DCS, G–2. Obtain MDI support and guidance to technology base programs, to .
validated online lifecycle threat volt
Threat resources and reports that assist Acq/Intel analysts in support of their PMs include: Defense Intelligence Agency’s (DIA) Defense Intelligence Threat Library modules, DIA and IPC VOLT Reports, Critical .I. SECTION I - DOCTRINAL AND ORGANIZATIONAL TEST SUPPORT PACKAGE (CONT' D) PAGE 5.0 TEST SETTING 5.1 General 20 5.2 PR Operation/Maintenance 20 5.3 Decontamination 20 5.4 Limitation 21 II. SECTION II - THREAT SUPPORT PACKAGE 1.0 REFERENCE 22 2.0 THREAT 22 III. SECTION III - TRAINING SUPPORT PACKAGE 1.0 .Test and Evaluation (DUSA-TE), provides oversight to the Joint Threat Support Branch for Chemical and Biological Defense to provide system threat assessments for joint CBRN defense equipment and develop Joint Threat Test Support Packages for programs within the CBDP. (2) The JRO-CBRND works in cooperation with the Joint Science and .We would like to show you a description here but the site won’t allow us.
Develops Validated On-Line Threat (VOLT) documents, provides input to Threat Test Support Packages (TTSPs), and educates the capability development enterprise on the future Fires OE. Supports the .
Threat Test Support Package (TTSP) Parts 1 & 2 2. Trusted agent(s) 3. Signed ROEs 4. OTA-TP or Modified Cybersecurity OTA-TP 5. PDRR Test Plan 6. AA Test Report 7. PDRR Test Report OT Cybersecurity Documentation Timeline 1. Security Classification Guide 2. Test timeframe, location, unit 3. Test and Evaluation Master Plan TGVS Computer Network Operations (CNO) Annex to the Threat Test Support Package. The OTA will conduct the assessment in the context of TGVS mission operations, with representative data sources, network traffic, and external interface connectivity; the proposed test boundary is shown in Figure 3-2. Threat test support package a. Purpose. The TTSP is the baseline threat document for a specific test to describe the threat to be portrayed, specific guidance on threat targets and countermeasures, and how the threat fits into the overall T&E requirements. – DoD test facilities can only test 21% of high -priority RF threats and 22% of medium - and low-priority RF threats in a specific theater of operations – For worldwide IR, tests can be conducted against only 28% of high -priority threats and 26% of medium- and low-priority threats • Ensure DoD can sufficiently test and train
-Report and OT Threat Test Support Package . UNCLASSIFIED TRADOC G2 Threat Support to U.S. Army Training & Acquisition U.SNNY Intel Production Centers DNI DIA DA G2 TRADOC G2 TRADOC Threat Managers AMC G2 AMC FIOs TACOM CECOM AMCOM RDECOM ATEC NGIC ONI MSIC Fires Center of Excellence; Fort Sill, OK1. Threat Test Support Package (TTSP) Parts 1 & 2 2. Trusted agent(s) 3. Signed ROEs 4. OTA-TP or Modified Cybersecurity OTA-TP 5. PDRR Test Plan 6. AA Test Report 7. PDRR Test Report OT Cybersecurity Documentation Timeline –Guide 1. Security Classification Guide 2. Test timeframe, location, unit 3. Test and Evaluation Master Plan 4.
Threat test support package A document, or group of documents, that provide a comprehensive description of the threat to a U.S. system that is being tested and the targets that the system will engage. FOR THE COMMANDER: OFFICIAL: JOHN P. HERRLING Major General, GS Chief of Staff DAVID G. FITZ-ENZ Colonel, GS Deputy Chief of Staff for .o Modifies U.S. Army Training and Doctrine Command’s requirements to comply with higher headquarters revised guidance including use of Joint Capabilities Integration and DevelopmentAcronym Definition; TTSP: This Too Shall Pass: TTSP: Time Temperature Superposition Principle: TTSP: Talmud Torah of St. Paul (Jewish educational center; St. Paul, MN .
Modifications to current threat-support production methodology will create an efficient means to enable both large-scale STAR production and to standardize . will be included to highlight “most likely” threats. • Test Readiness Review STAR (TRR STAR): Delivered 90 days before the TRR, and shorter than 200 pages. The TRR(12) Ensure the integration of approved threat in user testing programs to include the preparation of test threat support packages in response to stated tester requirements. e. The Commanding General, U.S. Army Materiel Command will- (1) In coordination with TRADOC, prepare, review, and forward to OACSI for HQDA approval all threat statements .Proactive threat hunting: HUNTER's hunt packages allow organizations to proactively hunt for threats, reducing the risk of a successful attack and protecting their data and reputation. Expertly-crafted content: The hunt .(U) Threat begins network/system recon (U) Threat test Support Package developed (U) ROE established (U) Information collection to support CVPA and PDRR (U) CVPA (U) Adversarial Assessment (U) PDRR activities (U) Data includes •(U) Instrumented •(U) Survey •(U) Logs •(U) Field collection (U) Within 60-90 days after test
Develops Validated On-Line Threat (VOLT) documents, provides input to Threat Test Support Packages (TTSPs), and educates the capability development enterprise on the future Fires OE. Supports the .Threat Pursuit Virtual Machine (VM): A fully customizable, open-sourced Windows-based distribution focused on threat intelligence analysis and hunting designed for intel and malware analysts as well as threat hunters to get up and running quickly. - mandiant/ThreatPursuit-VMVirus & threat protection in Windows Security helps you scan for threats on your device. You can also run different types of scans, see the results of your previous virus and threat scans, and get the latest protection offered by Microsoft Defender Antivirus. Under Current threats you can: See any threats currently found on your device. The Validated Online Lifecycle Threat (VOLT) Report is a regulatory document for Acquisition Category (ACAT) I-III programs. These programs require a unique, system-specific VOLT Report to support capability development and PM assessments of mission needs and capability gaps against likely threat capabilities at Initial Operational Capability (IOC).
information in the threat is inconsistent, implausible, or it lacks detail. A threat should be considered MEDIUM RISK if it has an increased level of realism. Meaning that an attack could be carried out, but it does not appear entirely realistic. A HIGH RISK threat is when the threat is direct, specific, and realistic. The threat might
Threat test support package † 4–4, page 18 Program protection plan † 4–5, page 19 Appendixes A. References, page 20 B. System Threat Assessment Report Format, page 22 C. Threat Test Support Package Formats, page 24 D. Management Control Evaluation Checklist, page 25 Glossary AR 381–11 † 26 January 2007 iii. Chapter 1Study with Quizlet and memorize flashcards containing terms like which best describes the terrorist planning cycle?, homegrown violent extremists (hve) are never us citizens or legal residents, a domestic violent extremist (dve) conduct attacks in support of and more.
Based on the description provided, how many insider threat indicators are present? Elyse has worked for a DoD agency for more than 10 years. She is a diligent employee who receives excellent performance reviews and is a valued team member. She has two children and takes them on a weeklong beach vacation every summer.Partners can use CTEPs to initiate discussions within their organizations about their ability to address a variety of threat scenarios. Each package is customizable and includes template exercise objectives, scenarios, and discussion questions as well as a collection of references and resources. . Exercise Planning and Conduct Support .
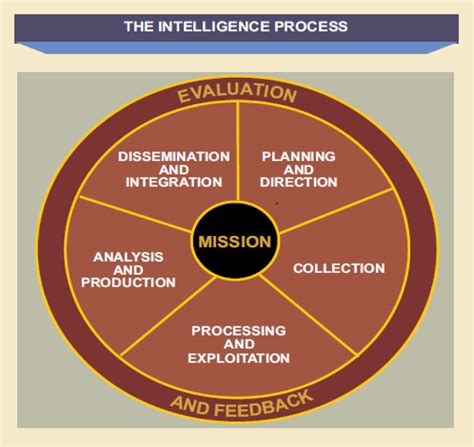
intelligence supportability analysis
best cases for iphone x drop test
intel support to targeting
PC Game - SexNote v0.22.0b [ENG][ESP][PTBR] - FGAMES
threat test support package|intel support to targeting